
Uncover Cyber Threat from
the Depth of Dark Web.
External threats evolve fast—shadow IT, leaked credentials, phishing, and hidden risks. Gaining full visibility before attackers strike is a big chalenge.
Let’s take a closer look on what problems we are facing.
Most companies still rely on a reactive approach to cyber threats—responding only after an attack has occurred. Without predictive threat intelligence, organizations fail to anticipate threats, leaving them vulnerable to data breaches, financial losses, and operational disruptions. By the time an attack is detected, the damage is already done, and recovery costs skyrocket.
Learn How Cyfirma Can Handle This Case
Many organizations struggle with hidden compliance gaps and unchecked risk exposure due to evolving regulations, unmonitored digital assets, and a lack of real-time threat intelligence. Forgotten public assets, leaked credentials, and unpatched vulnerabilities can lead to non-compliance, regulatory penalties, and increased cyber risks, leaving organizations exposed to potential attacks.
Learn How Cyfirma Can Handle This Case
You can’t protect what you can’t see. Limited visibility into your external attack surface leaves exposed assets—unmonitored domains, cloud services, or misconfigured systems—vulnerable to cyber threats. Attackers actively seek out these blind spots to exploit, leading to data breaches, financial loss, and operational disruption. Without complete visibility, your organization remains a step behind the threats.
Learn How Cyfirma Can Handle This Case
Cybercriminals exploit trust by impersonating brands, executives, and employees through fake websites, emails, and social media profiles. These scams fuel phishing attacks, credential theft, and financial fraud—damaging corporate reputation and putting individuals at risk. Without proactive monitoring, businesses and people remain vulnerable to deception, data breaches, and financial loss.
Learn How Cyfirma Can Handle This Case
What’s being said about your company outside your network matters. Discussions on forums, social media, and dark web marketplaces can reveal emerging threats, leaked data, or reputational risks—but without visibility, businesses remain unaware. Failing to monitor these external insights leaves organizations blind to potential attacks, misinformation, and shifting public perception, making them reactive rather than proactive.
Learn How Cyfirma Can Handle This Case



INTRODUCING
CYFIRMA
CYFIRMA is a cybersecurity tool specializing in External Threat Landscape Management (ETLM). Its flagship platform, DeCYFIR, provides proactive threat intelligence by analyzing cyber threats from an outside-in perspective.
You may already be familiar with vulnerability assessment products that focus on detecting vulnerabilities, making it harder for hackers to penetrate your system.
However, what you might not know is the hackers' visibility into your data—leaked credentials, exposed assets, and the intentions of threat actors lurking across the web. These factors play a crucial role in the success of a cyberattack.
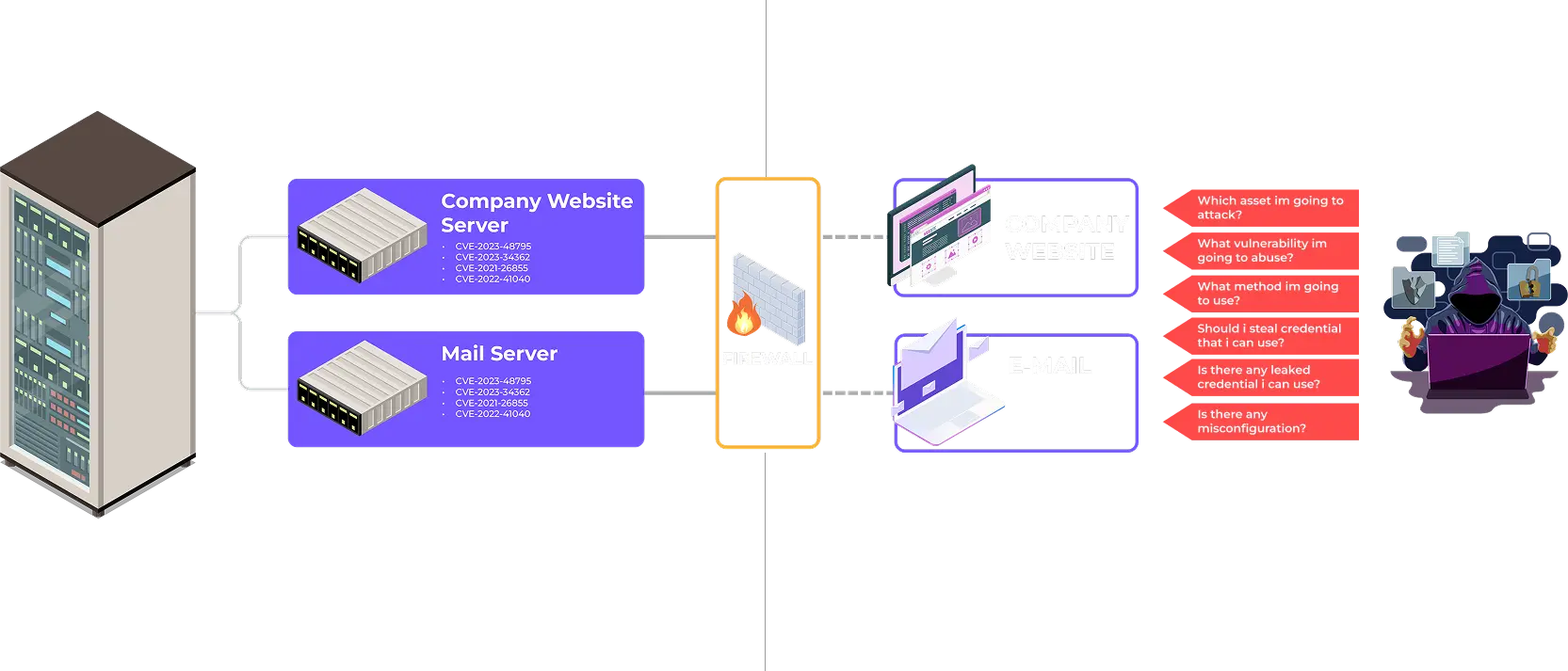
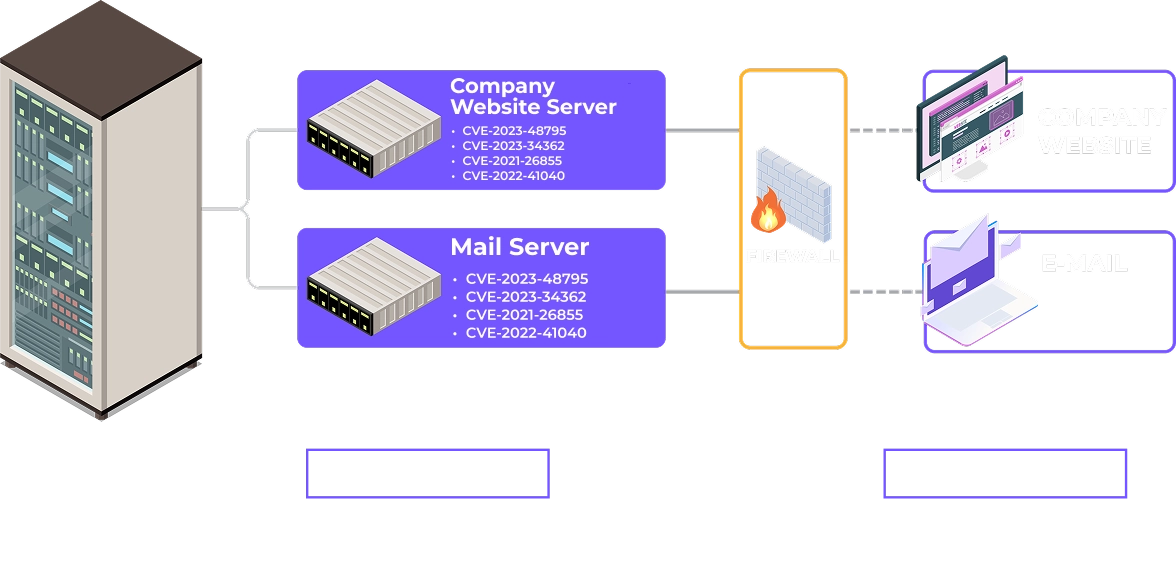
OFFICE AREA
USER AREA
This is where CYFIRMA comes in, collecting and correlating threat intelligence from across the web to provide actionable insights and proactive defense against cyber threats.
ACTIONABLE INSIGHTS
Get a comprehensive list of all publicly exposed assets.
Detect vulnerabilities in assets accessible to the public.
Track mentions of your company across public platforms.
Discover discussions about your company on dark web forums.
Gain intelligence on threat actors targeting your organization.
Detect exposed credentials before they’re exploited.
Identify fraudulent activities misusing your brand and key personnel.
Stay Ahead of Hackers by Predicting
Their Next Move Before They Strike.
Most organizations react to cyber threats only after they occur, leaving them exposed to evolving attacks. CYFIRMA changes this with a predictive, intelligence-led approach to stay ahead of threats.
CYFIRMA uncovers who is targeting your organization, their motives, and potential attack methods so you can proactively strengthen defenses.
Identifies exposed assets, misconfigurations, and high-risk vulnerabilities that threat actors might exploit, helping security teams focus on critical weaknesses.
Cyfirma Risk Scoring system intelligently correlates data from multiple sources—threat actor activities, vulnerabilities, leaked credentials, and dark web discussions—to assess which risks pose the greatest danger to your organization. By analyzing and scoring threats based on real-time intelligence, security teams can focus on the most critical risks first, ensuring a proactive and efficient defense.
CYFIRMA correlates domains, CVEs, threat actors, leaked data, and vulnerabilities to reveal hidden connections. By mapping threat relationships, it provides actionable insights, enabling security teams to predict and prevent attacks before they happen.
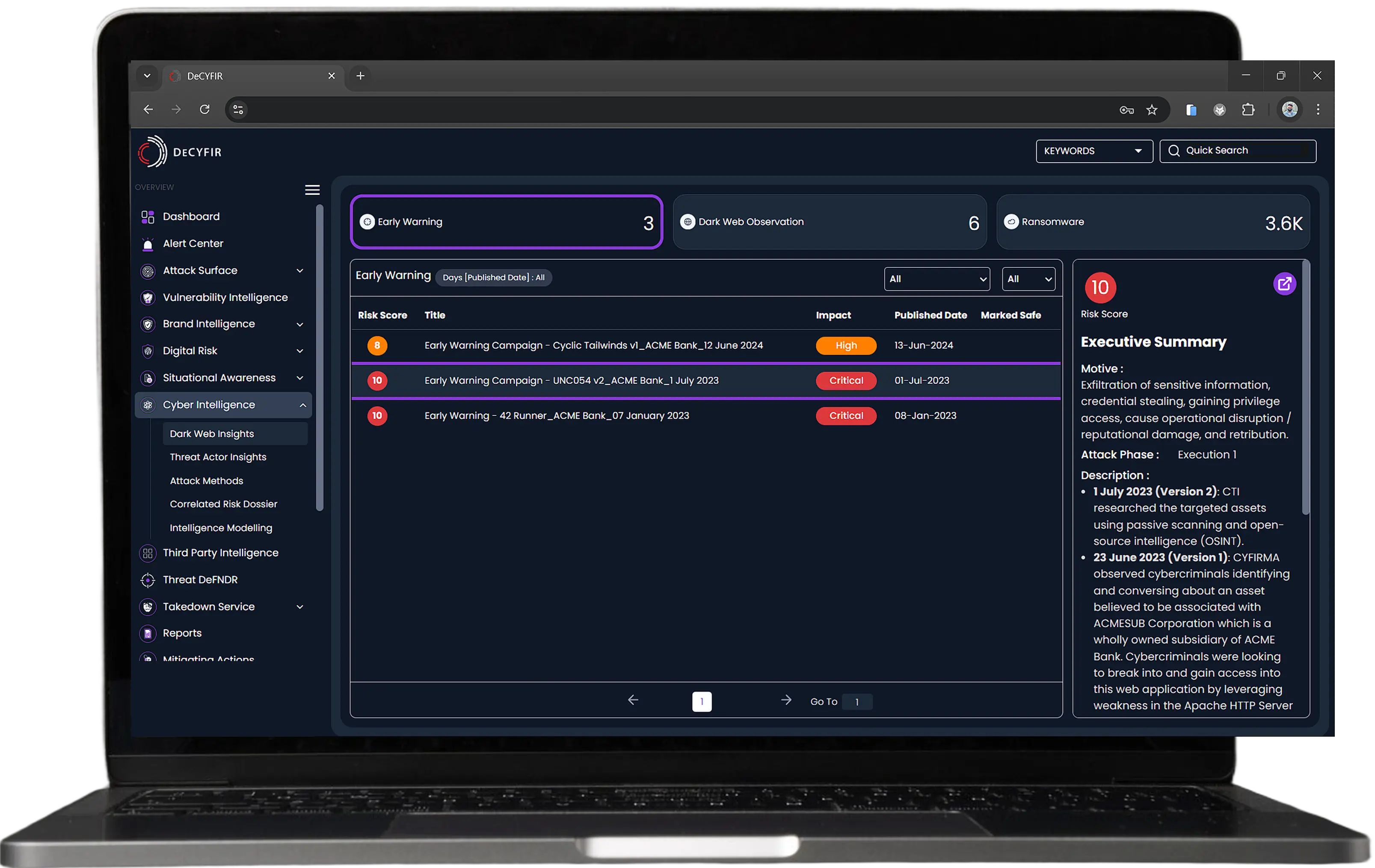
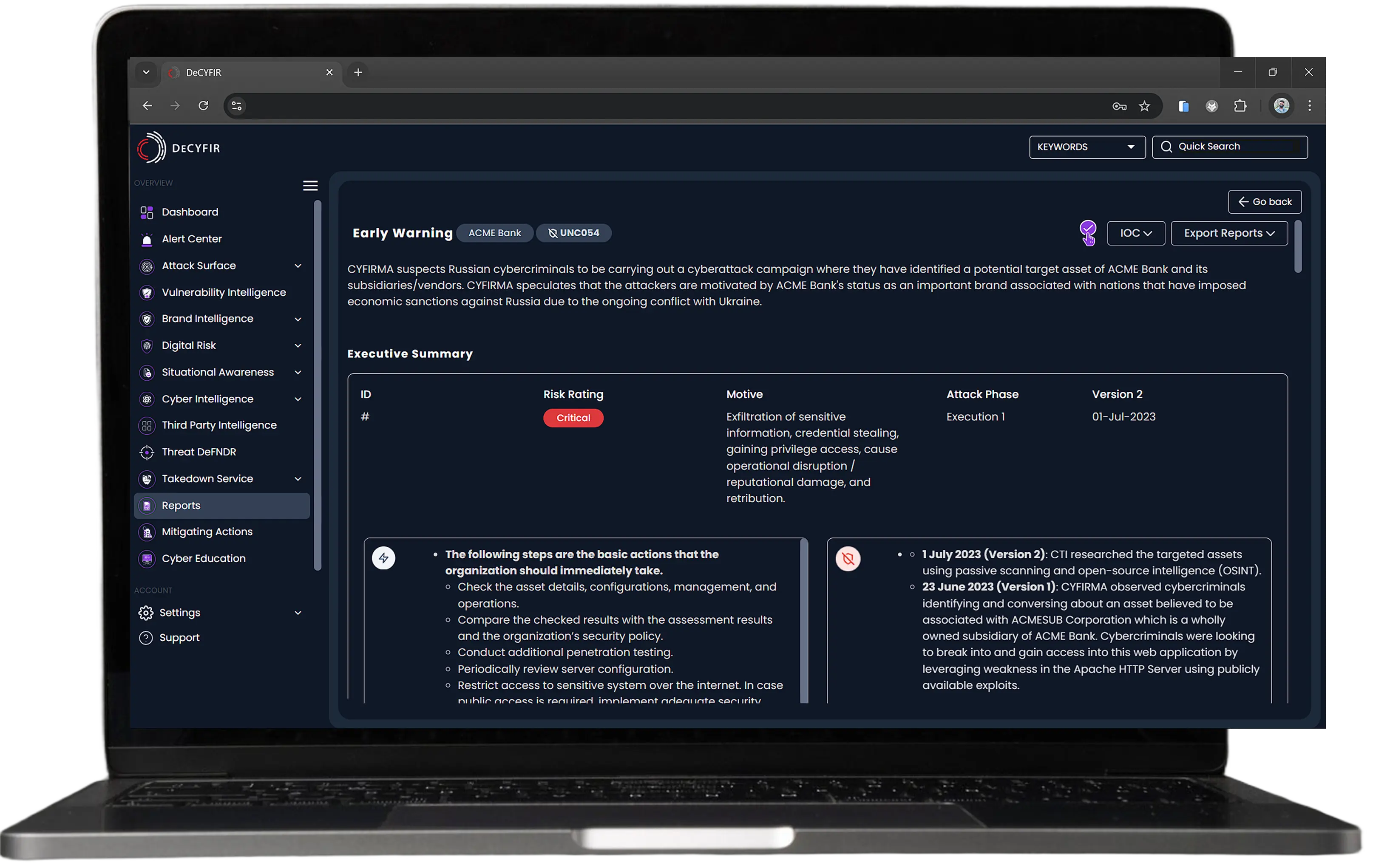
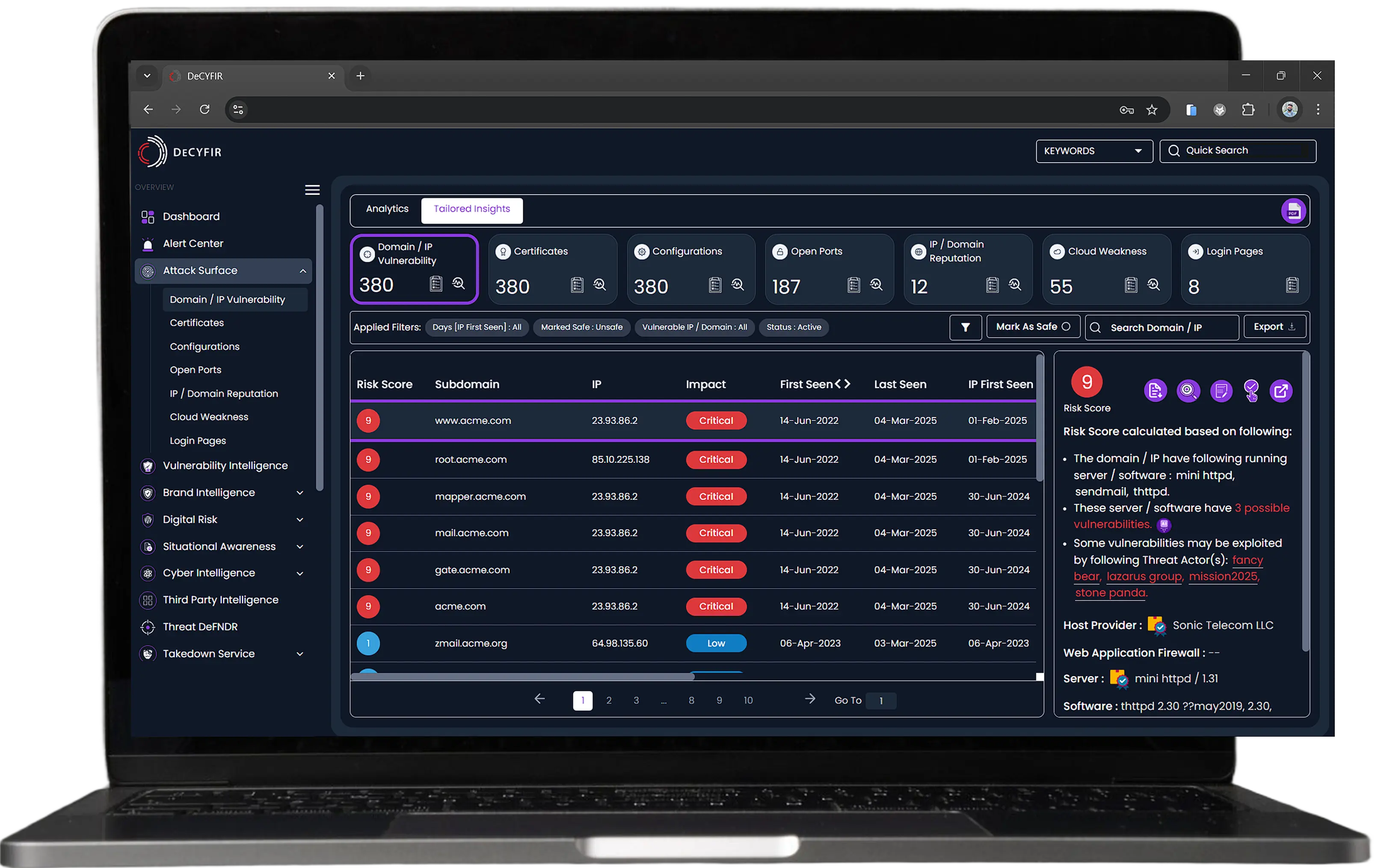
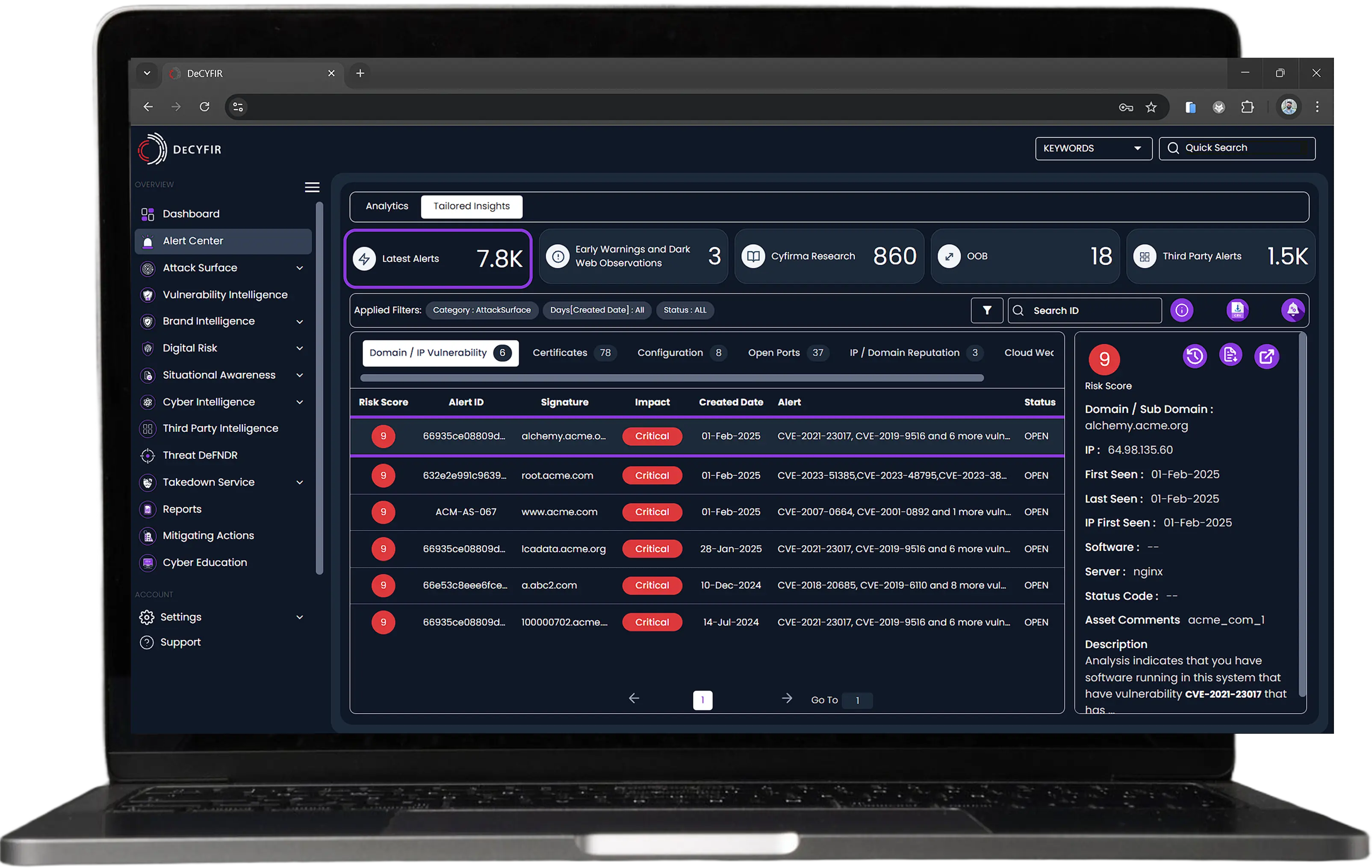
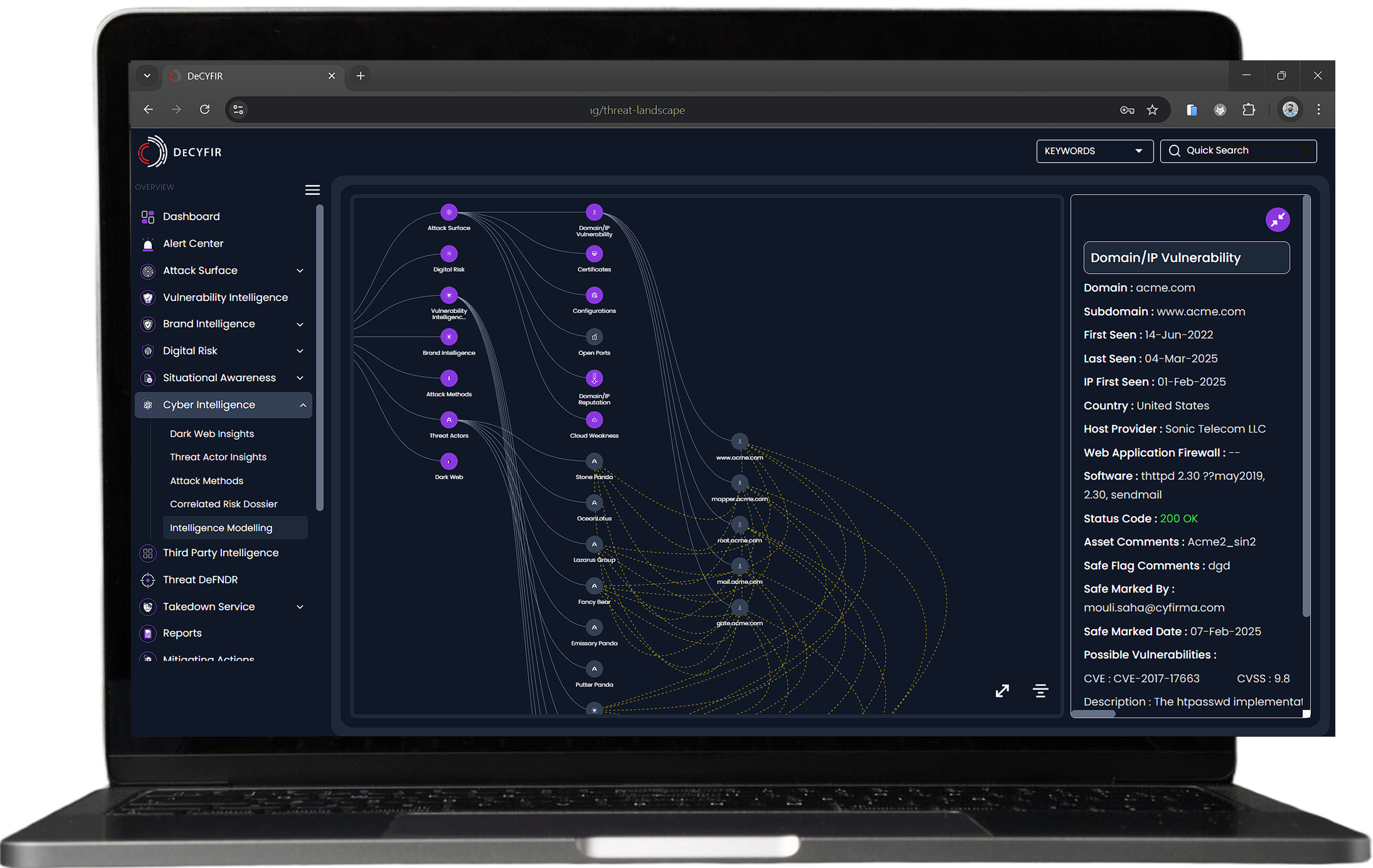
Stay Compliant, Reduce Risk
Exposure, and Strengthen
Cybersecurity Resilience
Ensuring compliance with evolving regulations like OJK requirements is a challenge for many organizations. Hidden compliance gaps, forgotten assets, and unchecked vulnerabilities can lead to regulatory penalties, security breaches, and reputational damage. Financial institutions must safeguard sensitive data, secure digital assets, and proactively mitigate cyber risks—yet many struggle with data leaks, misconfigurations, and increasing regulatory demands.
CYFIRMA empowers organizations to stay ahead of compliance requirements and strengthen cybersecurity resilience by:
Detect Vulnerabilities, Open Ports, Misconfiguration on Forgotten Assets
Forgotten public assets can become vulnerable entry points for cyber threats, expanding your organization’s attack surface and creating compliance risks. CYFIRMA scans externally to identify what is visible to attackers, detecting forgotten or unprotected assets that may have been overlooked. By providing actionable insights, CYFIRMA enables security teams to identify, assess, and secure exposed assets before they can be exploited—helping organizations not only strengthen cybersecurity but also maintain compliance by addressing potential regulatory gaps.
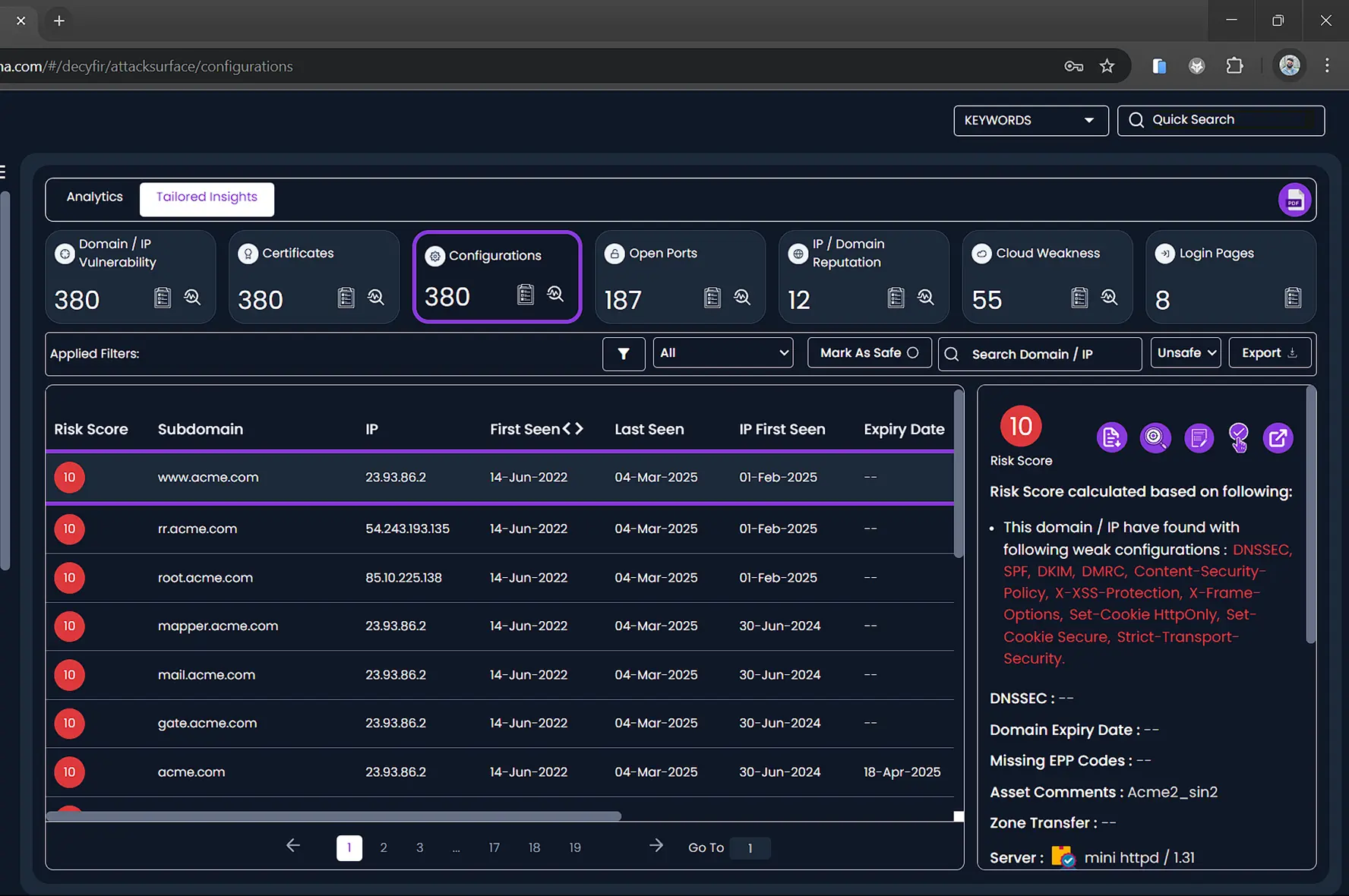
Detailed Insight on Attack Surface Including Vulnerabilities, Open Ports and Misconfiguration, etc.
Misconfigurations and unpatched vulnerabilities are among the leading causes of cyber incidents and compliance violations. CYFIRMA continuously scans your systems, networks, and exposed assets to detect security weaknesses before attackers do. By identifying misconfigurations and vulnerabilities in real-time, organizations can proactively address risks, prevent breaches, and maintain compliance with industry regulations.
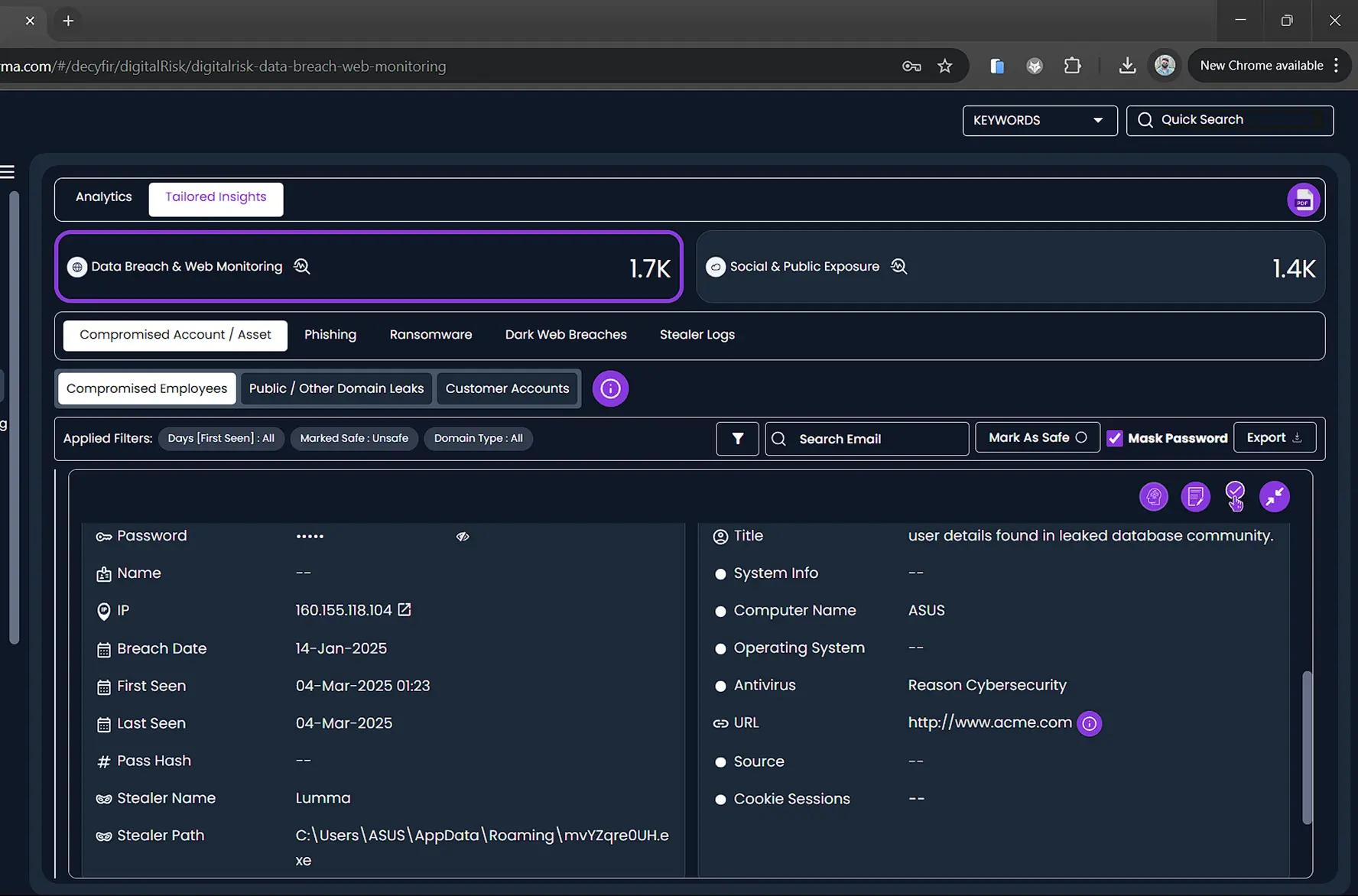
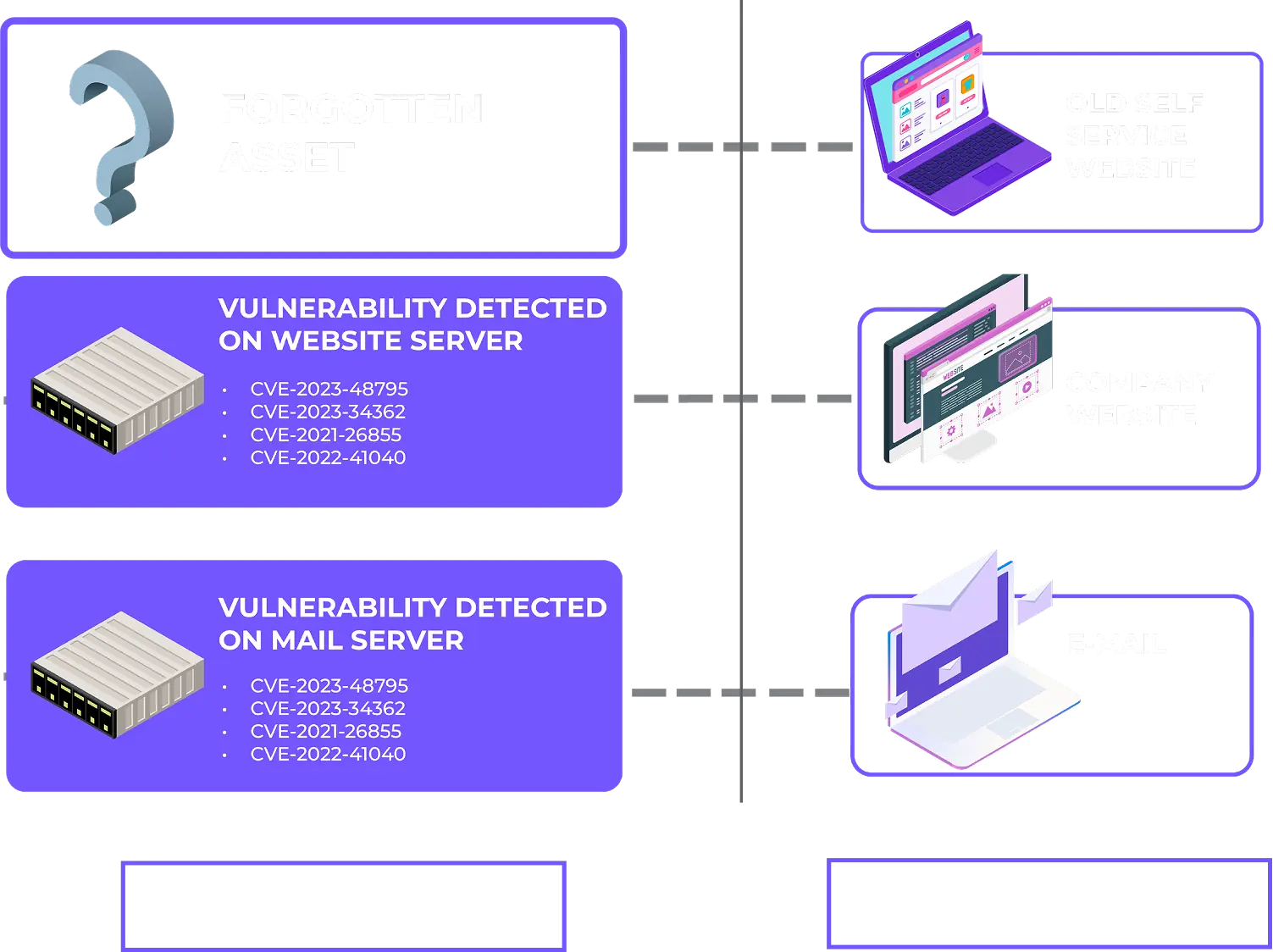
Give Insight on Leaked Credentials and Data Breaches
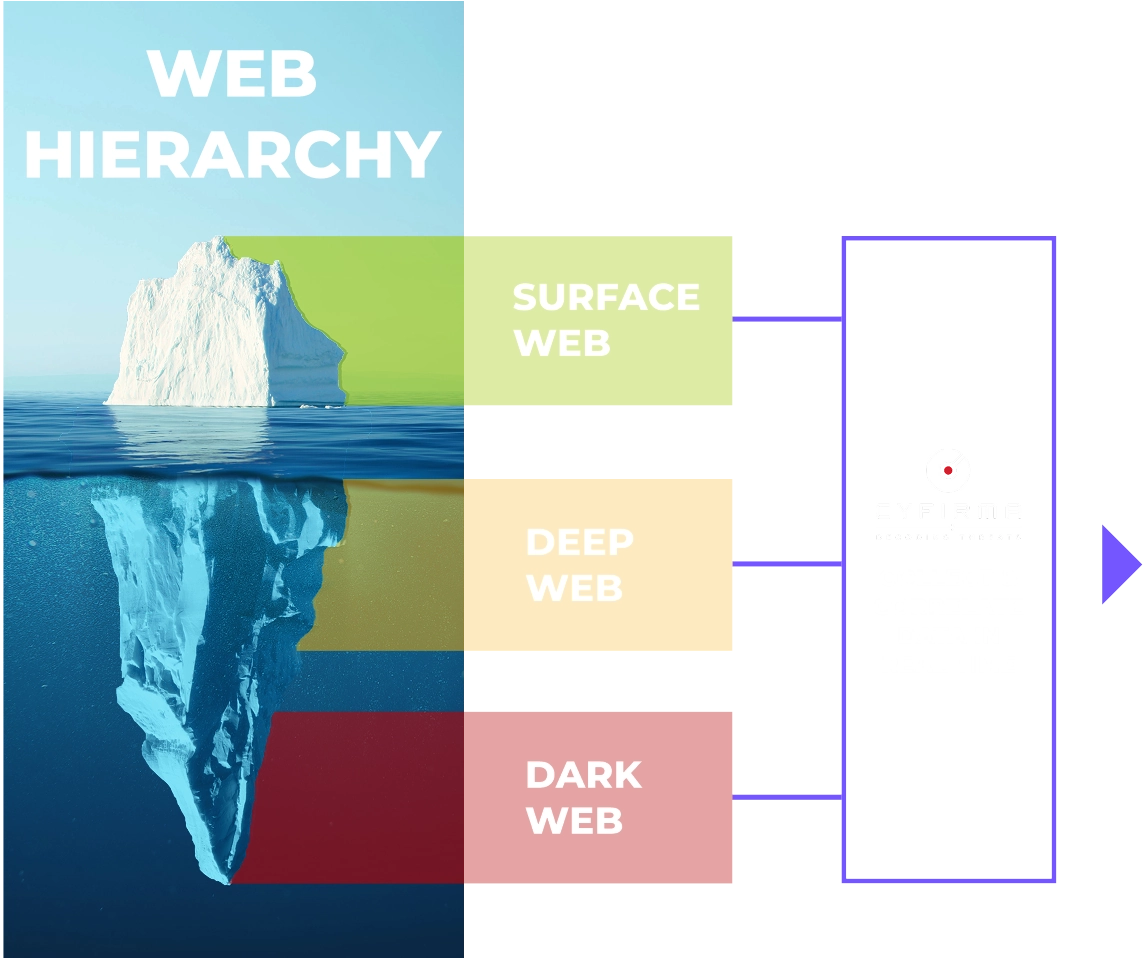
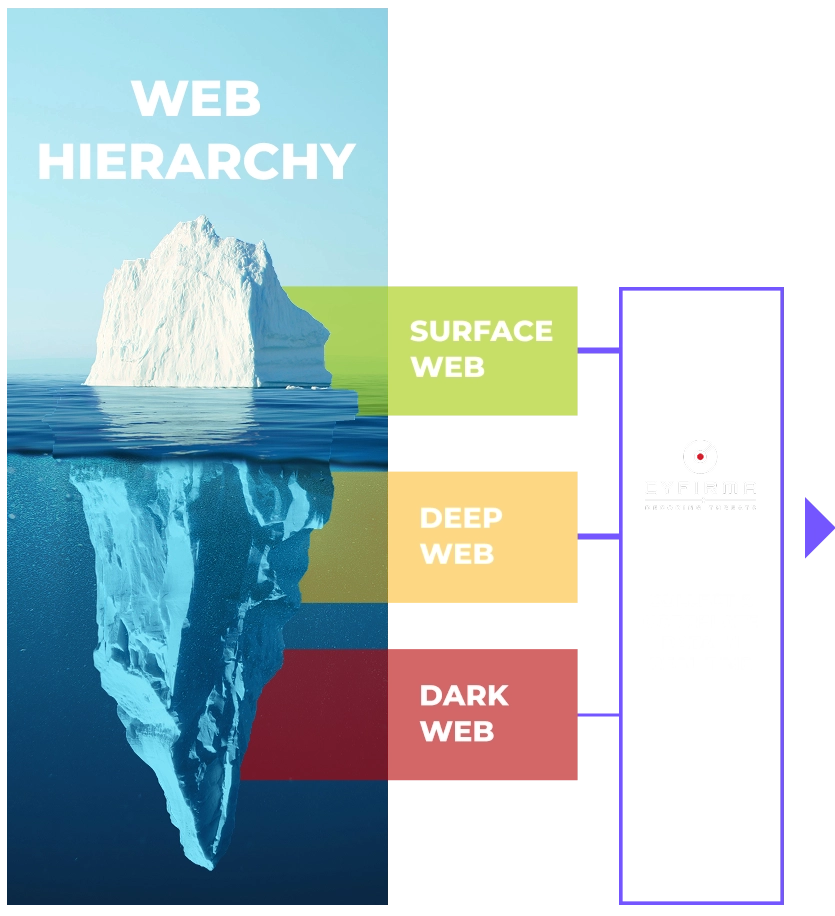
Leaked credentials and sensitive data are prime targets for cybercriminals, exposing businesses to cyberattacks and regulatory non-compliance. CYFIRMA monitors the surface web, deep web, and dark web to detect compromised credentials and exposed data linked to your organization. With early warnings and actionable insights, security teams can secure accounts, prevent breaches, and maintain compliance with data protection regulations.
Handle Phising, Fraud, Brand Impersonation with Ease
Cybercriminals fake domains, impersonate executives, and launch phishing attacks, putting your brand and customers at risk. CYFIRMA detects threats early, enabling swift action to takedown impersonators and prevent fraud.



Detect Similar Domains Impersonating Your Brand.
CYFIRMA monitors the internet for domain registrations and DNS changes to identify fraudulent websites using lookalike domain names (e.g., slight misspellings or extra characters) that cybercriminals create to deceive users.

Uncover Defaced Websites Mimicking Yours.
By continuously scanning surface web, deep web, and dark web sources, CYFIRMA detects cloned or defaced versions of your website that could mislead visitors and damage your brand reputation.

Spot Fake Mobile Apps Imitating Your Business
CYFIRMA scans official app stores (Google Play, Apple App Store) and third-party marketplaces to identify unauthorized apps using your brand name, logo, or content, which may be used for fraud, phishing, or malware distribution.

Identify Fake Executives or Impersonated Employees
Using AI-driven threat intelligence and social media monitoring, CYFIRMA detects impersonation attempts where cybercriminals create fake social media profiles, email accounts, or fraudulent websites posing as company executives or employees to conduct scams.
Request Takedowns
for Comfirmed Impersonation
CYFIRMA helps you eliminate fraudulent websites and impersonation threats by identifying, reviewing, and requesting takedowns of fake domains, phishing sites, and malicious content. Our streamlined process ensures swift action to protect your brand, customers, and digital assets from cybercriminals. protect your brand, customers, and digital assets from cybercriminals.
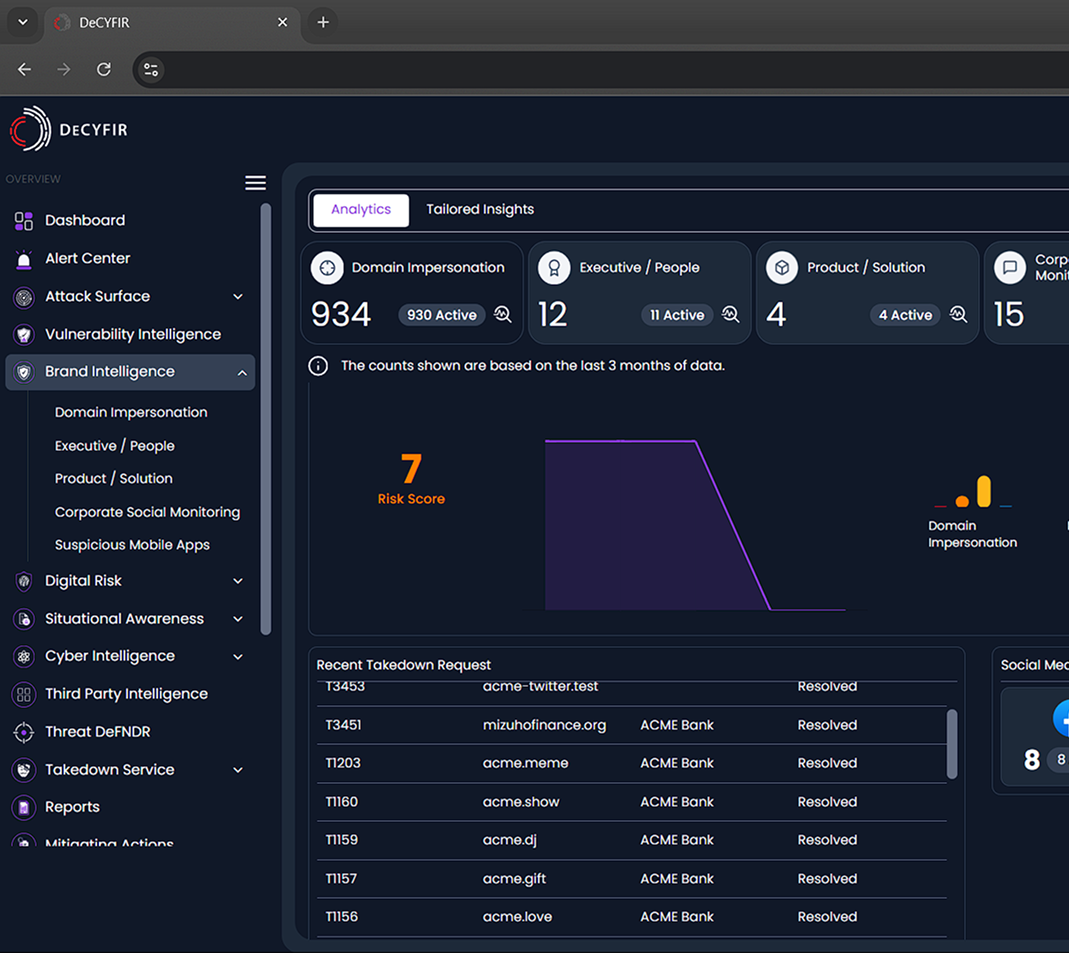

Know Planned Conversations in the Dark Web
Cybercriminals discuss targets, plan attacks, and trade stolen data in hidden forums. CYFIRMA monitors the dark web, uncovering threats linked to your organization, so you can act before an attack materializes.
Know Public Perception of Your Company
Negative sentiment, misinformation, or brand impersonation on the surface web can harm your reputation. CYFIRMA tracks online discussions, news, and social media sentiment, helping you stay ahead of potential crises and safeguard your brand image.
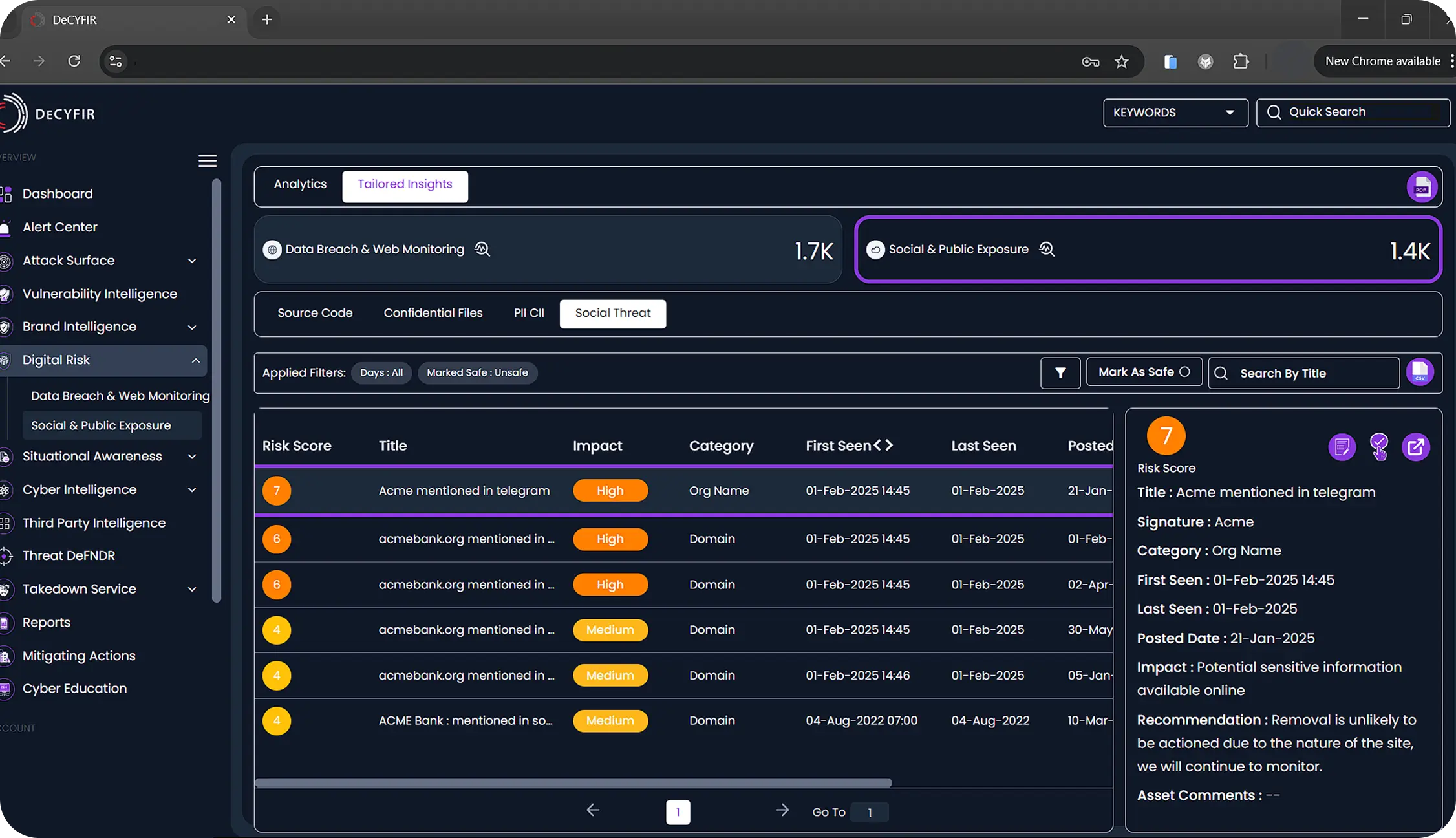
Stay Ahead of
Cybersecurity and Hacker Trends
Hackers continuously adapt, targeting new vulnerabilities and industries. CYFIRMA provides real-time intelligence on emerging threats, attack methods, and hacker activities, giving you situational awareness of cybersecurity trends worldwide. Stay informed, anticipate risks, and reinforce your defenses before threats materialize.

Common Use cases
Contact us for
Free Consultation!
Share your challenges, and we'll provide the best solutions for your business, Connecting with us is as simple as clicking a button, and let us come to you.


















