Powering Trust in
Every Mobile
Interaction.

Mobile is Growing Fast,
But So Are the Threats
Today, mobile apps do more than just serve a purpose, they connect people, power businesses, and make life easier. But behind every tap, swipe, and scroll… there could be a hidden threat waiting to strike.
76%
of apps store data insecurely
89%
can be exploited without physical access
56%
don't even need admin rights to be breached
57%
Android apps still suffer from weak security mechanisms
74%
iOS apps still suffer from weak security mechanisms
60%
of vulnerabilities exist on the client side
Let’s talk about
what attackers
already know.
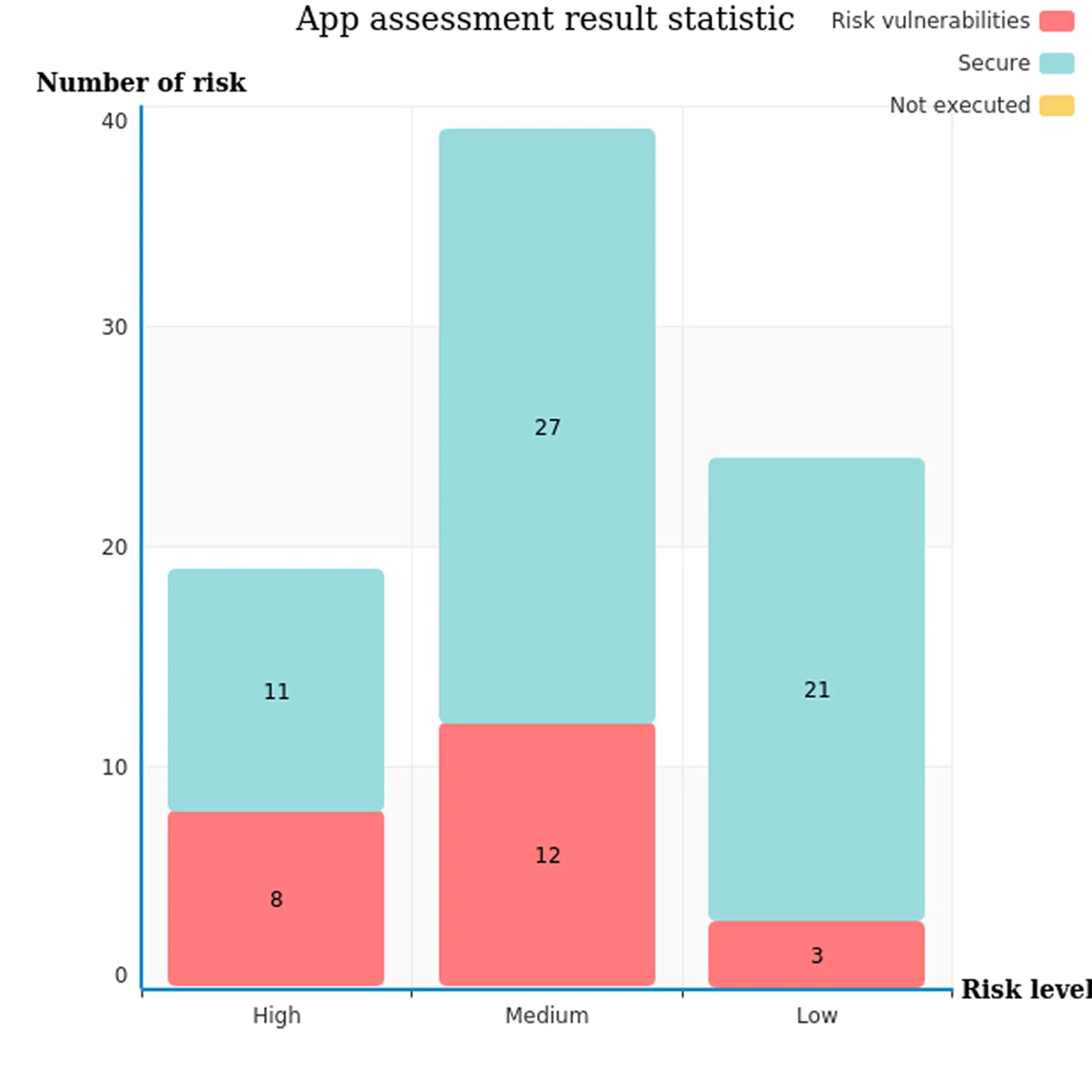
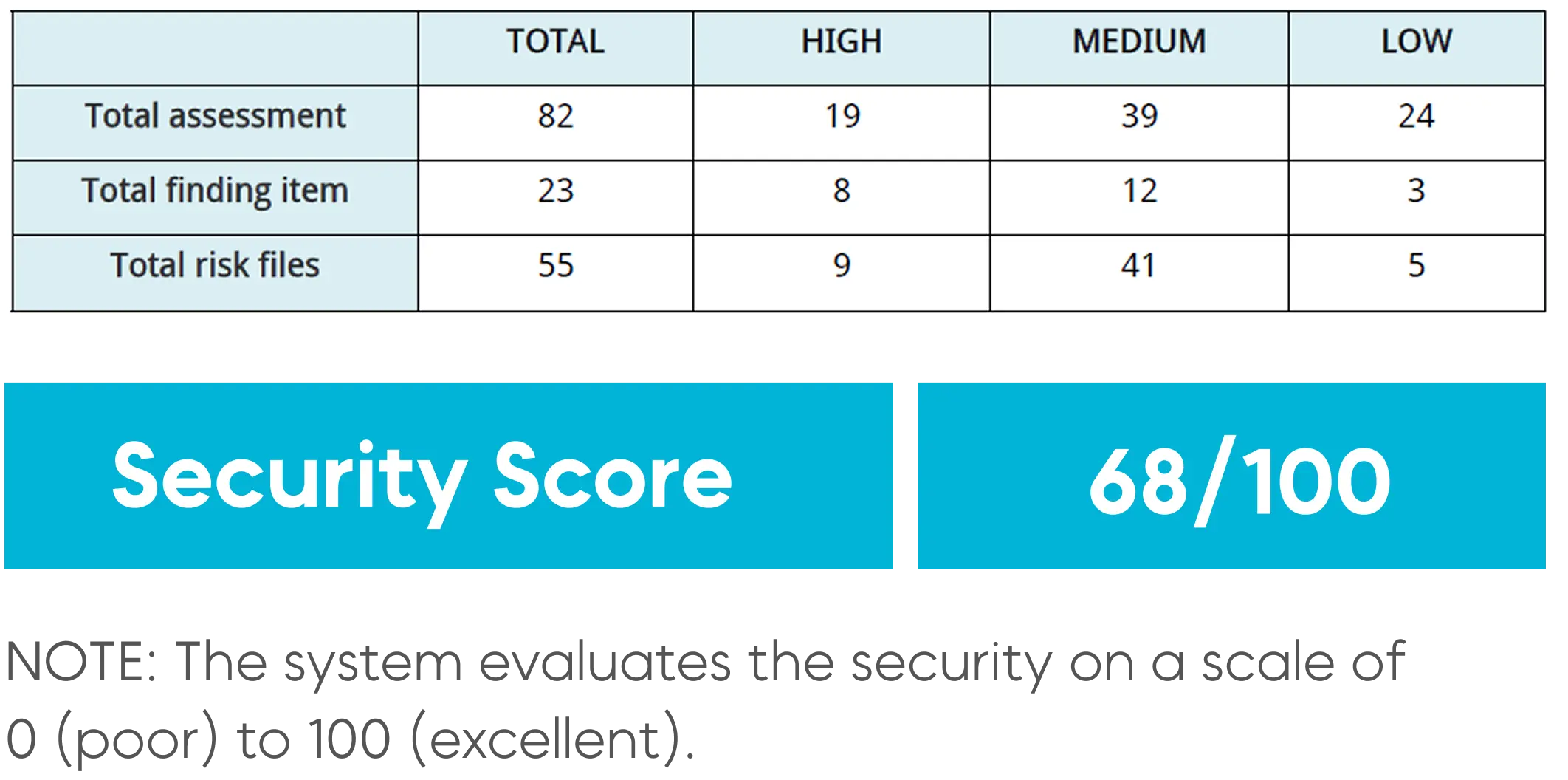
Is Your App Secure ?
Detect Threats Early
Check Your App's Compliance
Banking Has Gone Mobile,
But Has Security Caught Up?

A major study found 13 out of 14 mobile banking apps were vulnerable to attack.

76% could be exploited without physical access to the device.

Over a third can be breached without admin privileges.
Based on a study in 2019 on 14 fully featured mobile banking apps
100% of the apps contain vulnerabilities in their code.
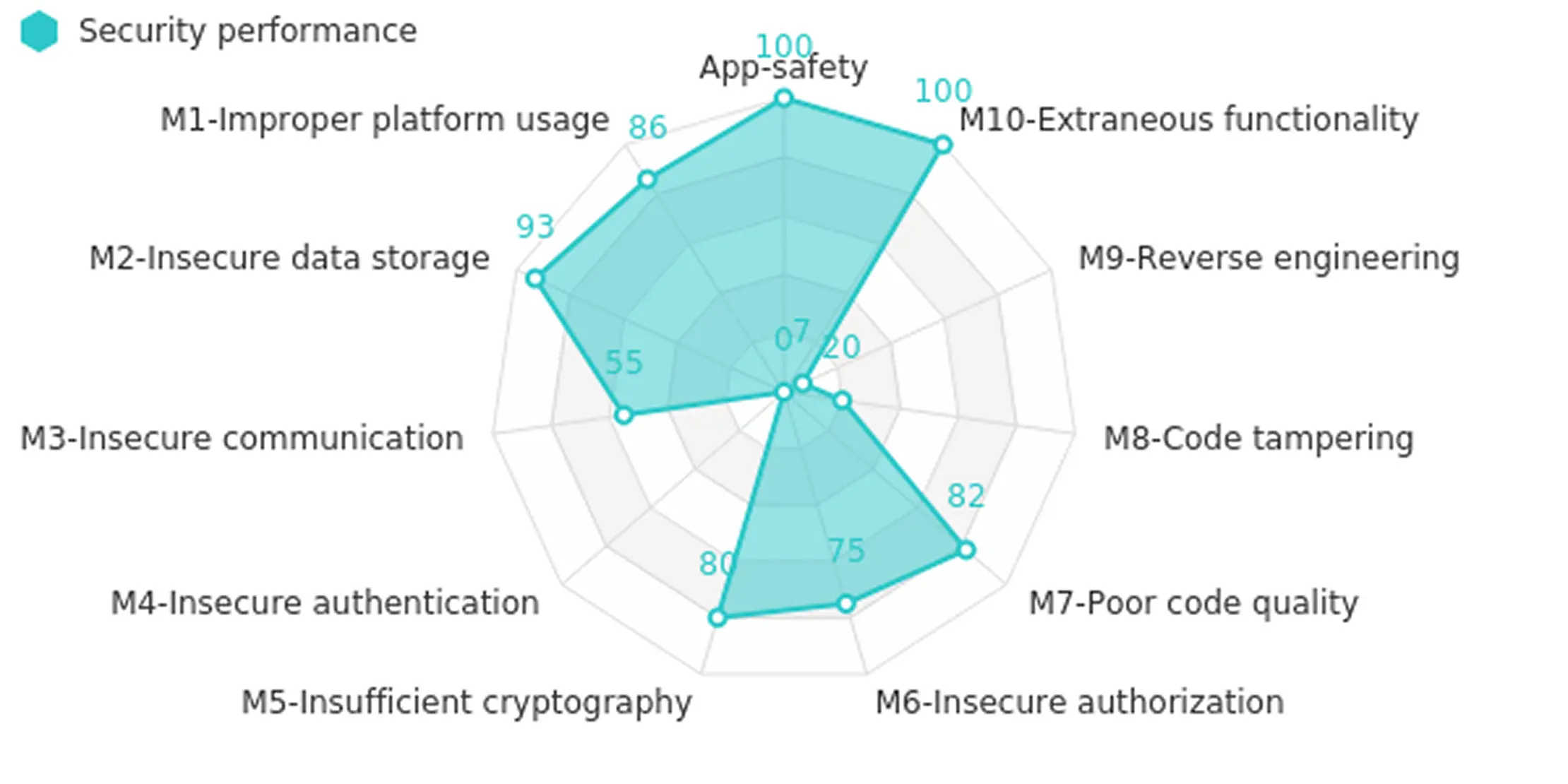
Hover over the chart to view details
SecIron detects threats like fake apps, phishing screens, code injection, and credential leak, before they can exploit your mobile app.
Let’s take a closer look on what problems we are facing.
Reverse engineering allows attackers to decompile and analyze your app’s code to uncover logic, vulnerabilities, or sensitive assets. Once exposed, they can clone the app, bypass security controls, or inject malicious behavior, all without your knowledge.
See How Seciron Solves This Problem
Sensitive information like user credentials, personal details, or payment data can be leaked due to weak encryption or improper storage. These leaks are often silent but deadly, damaging user trust and exposing your organization to compliance violations.
See How Seciron Solves This Problem
Third-party SDKs can become backdoors if not properly secured. Attackers may tamper with SDKs to insert malicious payloads or spyware, without altering the main app code. This makes the threat harder to detect and even harder to trace.
See How Seciron Solves This Problem
Tampering involves unauthorized modification of your app, such as changing behavior, disabling security checks, or adding malicious code. Tampered apps are often redistributed as fake versions, tricking users into trusting something dangerous.
See How Seciron Solves This Problem
If cryptographic keys are hardcoded or weakly protected, attackers can extract them to decrypt sensitive data, impersonate services, or forge tokens. One exposed key can compromise your entire security architecture.
See How Seciron Solves This Problem
Attackers may exploit app vulnerabilities to manipulate or hijack financial transactions, often rerouting funds or executing unauthorized transfers — leading to direct financial loss and user distrust.
See How Seciron Solves This Problem
Weak authentication mechanisms can be bypassed using techniques like session hijacking, brute force, or exploiting insecure logic. Once bypassed, attackers can gain access to privileged areas without being detected.
See How Seciron Solves This Problem
Malicious actors create counterfeit versions of your app, often embedding malware or phishing elements. Users are tricked into downloading these apps, thinking they’re legitimate, resulting in stolen credentials and reputational damage.
See How Seciron Solves This Problem
Fake login or input screens mimic the real interface of your app. Users unknowingly enter credentials into these fake screens, handing sensitive information directly to attackers in real time.
See How Seciron Solves This Problem
In MitM attacks, attackers intercept communication between your app and server — often by exploiting insecure Wi-Fi or certificates. They can steal session data, modify traffic, or impersonate the server itself.
See How Seciron Solves This Problem
Once an attacker breaks through your app’s core protections, all security assumptions collapse. Breached defenses open the door to lateral movement, persistence, and full exploitation, often undetected until significant damage is done.
See How Seciron Solves This Problem

Secure Coding Is No Longer Optional, It's a Regulatory Requirement
Otoritas Jasa Keuangan (OJK), through SE OJK No. 29/SEOJK.03/2022, officially mandates all banks to apply secure coding practices in system and application development.
SecIron Footprints:
Where Trust Begins
Since 2010, SecIron has been on a mission to make mobile apps safer, for businesses, developers, and the millions of users who trust them every day.
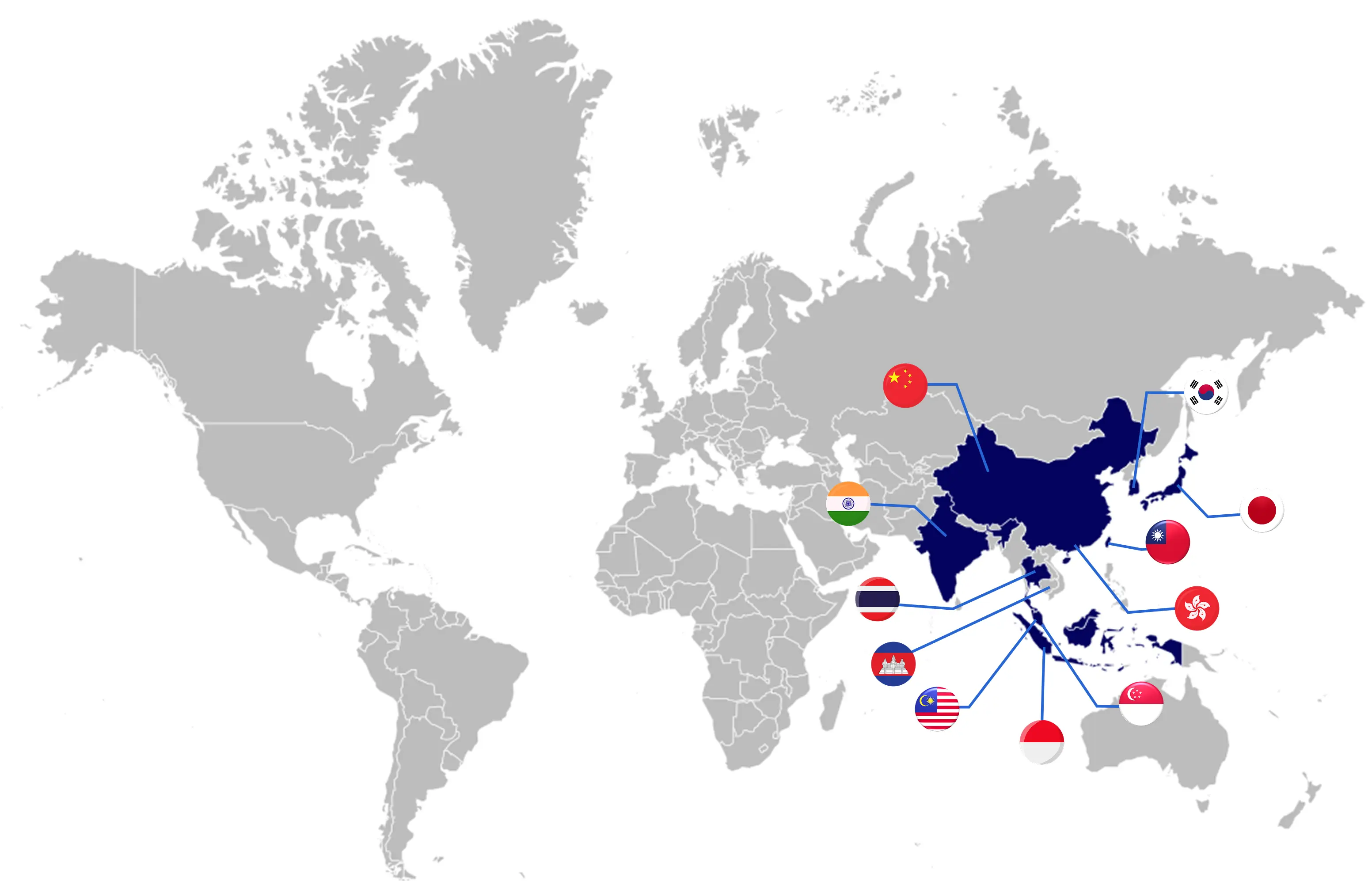
- 10,000+ apps secured
- Present in 11 countries across Asia
- Supported by 3 innovation, driven R&D centers
Everything You Need to Keep
Your App Safe
From development to deployment, SecIron empowers businesses to secure their mobile applications at every stage — with powerful products and expert-driven services.
Seciron Product

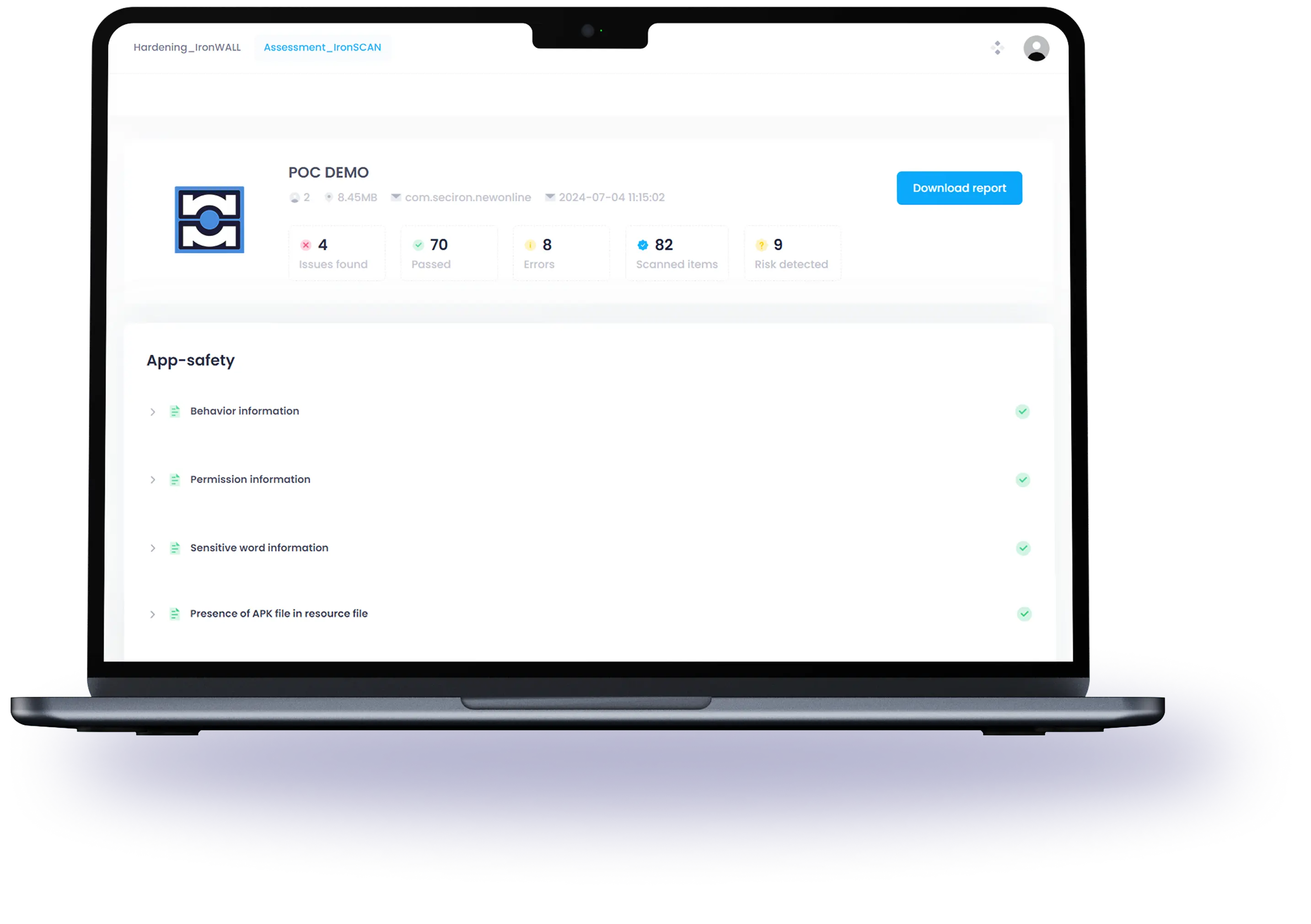
Vulnerabilities Assessment Platform
SecIron’s IronSCAN scans mobile apps to identify hidden vulnerabilities and provides clear, actionable recommendations to fix them before attackers strike.

Application Hardening Platform
IronWALL delivers robust hardening for Android and iOS apps, protecting against reverse engineering, code tampering, and data theft, without requiring any code changes.

Real-time Threat Monitoring & Response
IronSKY provides real-time visibility into mobile app threats, helping organizations detect, monitor, and respond instantly to malicious activity.
PEN-Test
SecIron’s mobile app penetration testing service simulates real-world attacks to uncover security weaknesses on both the business and client side of applications.
IronSKY Data Inspection Service
This service analyzes security data collected from devices to filter out false positives and detect signs of active hacking or compromise in the mobile environment.
SecIron Mobile App
Security Journey
SecIron secures your mobile app across every stage of its lifecycle, so you can launch with confidence and stay protected after going live.
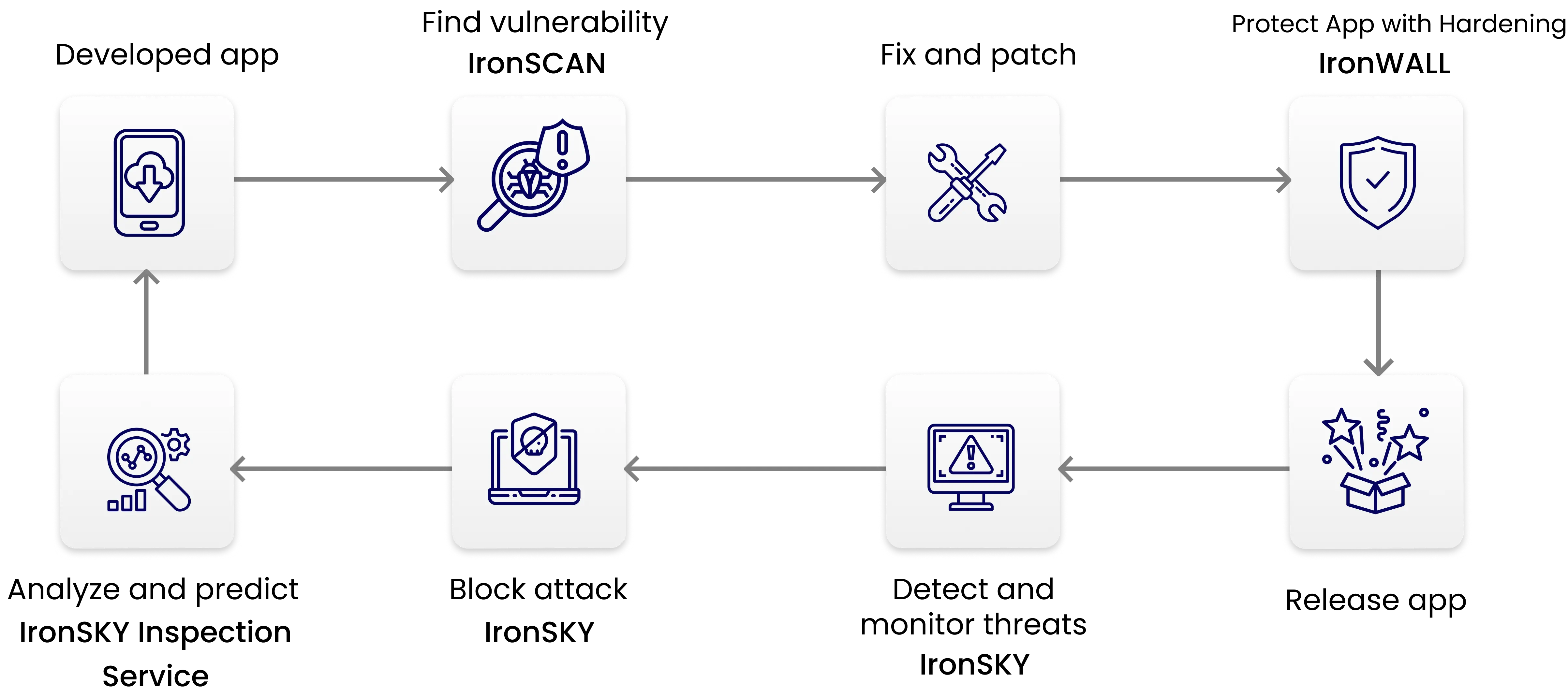
Secure Your App Smarter :

Mobile Application
Security Testing
To highlight the importance of mobile app security testing and position IronSCAN as a smart, fast, and reliable solution for identifying vulnerabilities before attackers do.
Test Your App Like a
Hacker
Mobile apps face real threats, and the best way to stay ahead is to think like an attacker.

Application Hardening
Platform
To emphasize the critical need for protecting mobile apps from tampering and position IronWALL as a powerful, seamless, and intelligent solution for hardening applications against reverse engineering and runtime attacks.
Comprehensive App Hardening,
Without the Complexity
Your mobile app is more than just code, it's your brand, your users, and your business. IronWALL protects all of it with seamless hardening that works behind the scenes.
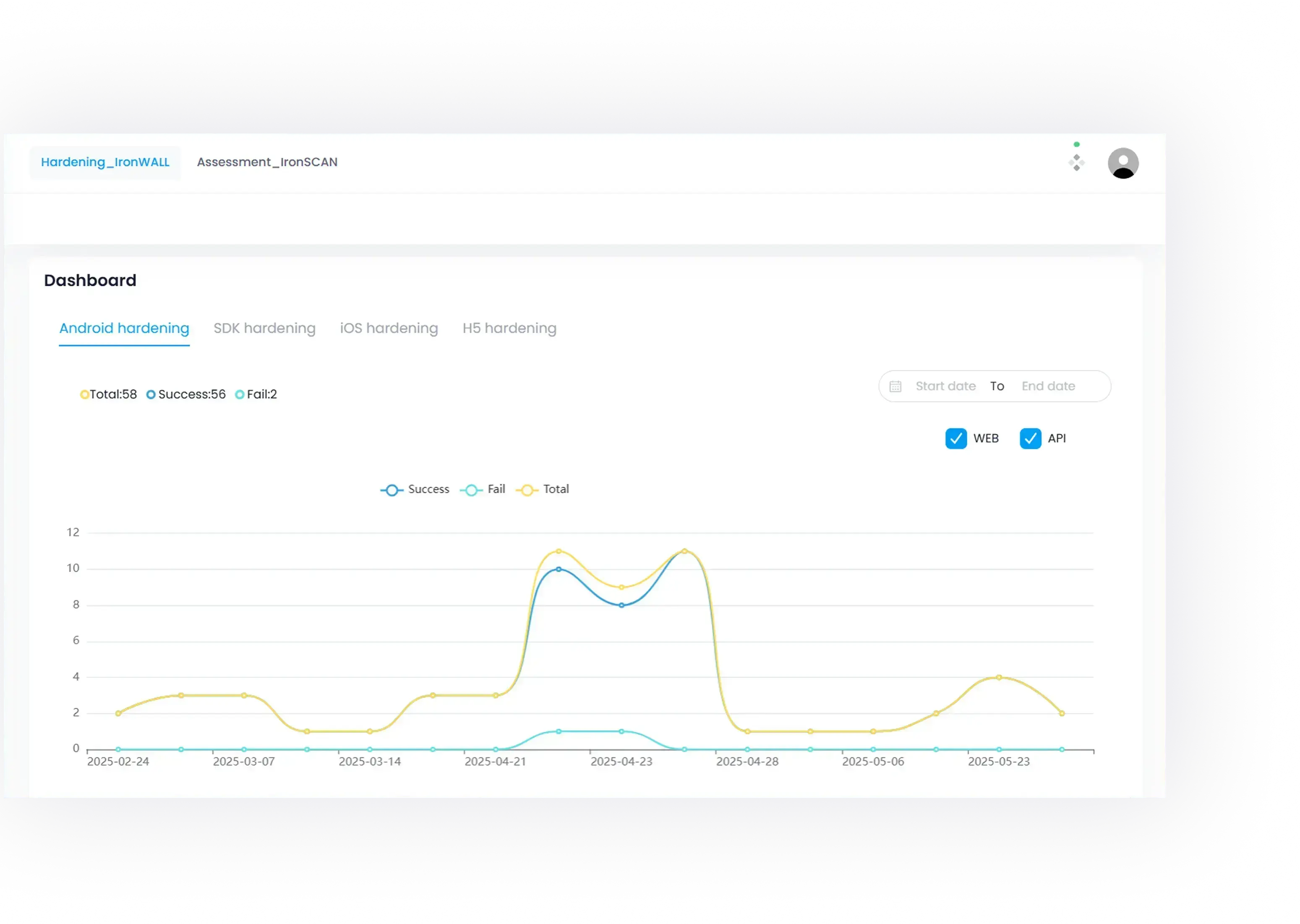
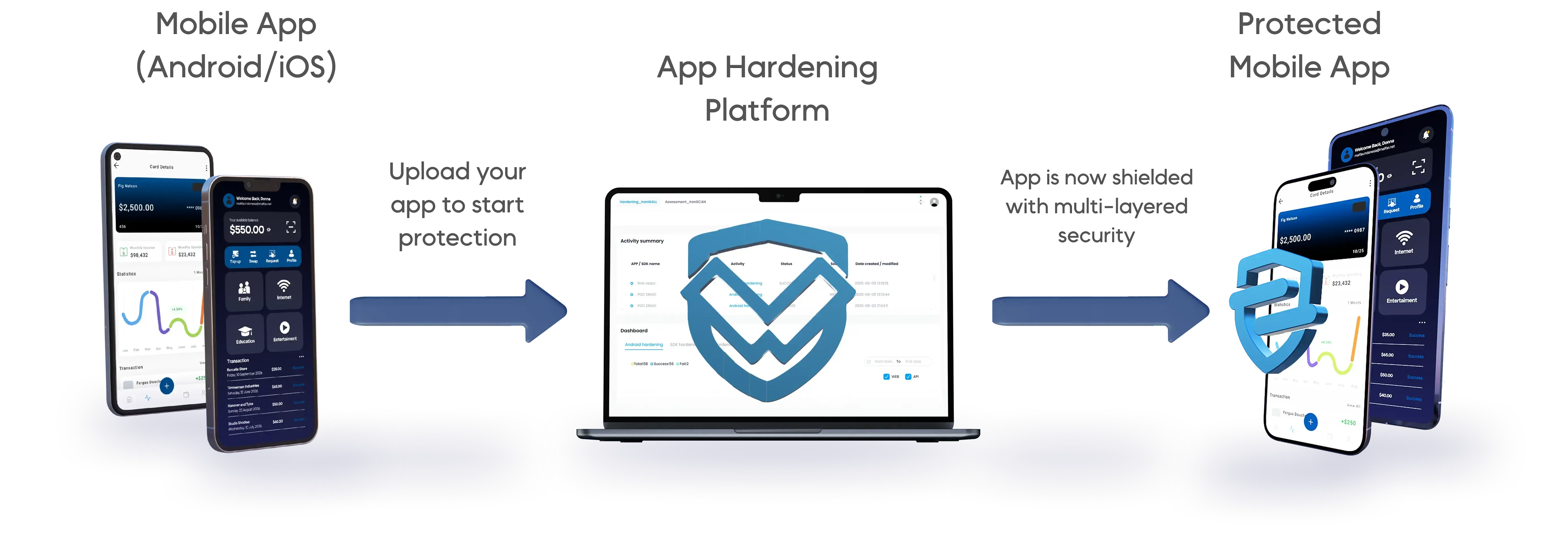
App Hardening Made Simple
SecIron’s IronWALL turns any mobile app into a well-protected asset, without complex coding or workflow disruption.
Real-time Threats
Monitoring System

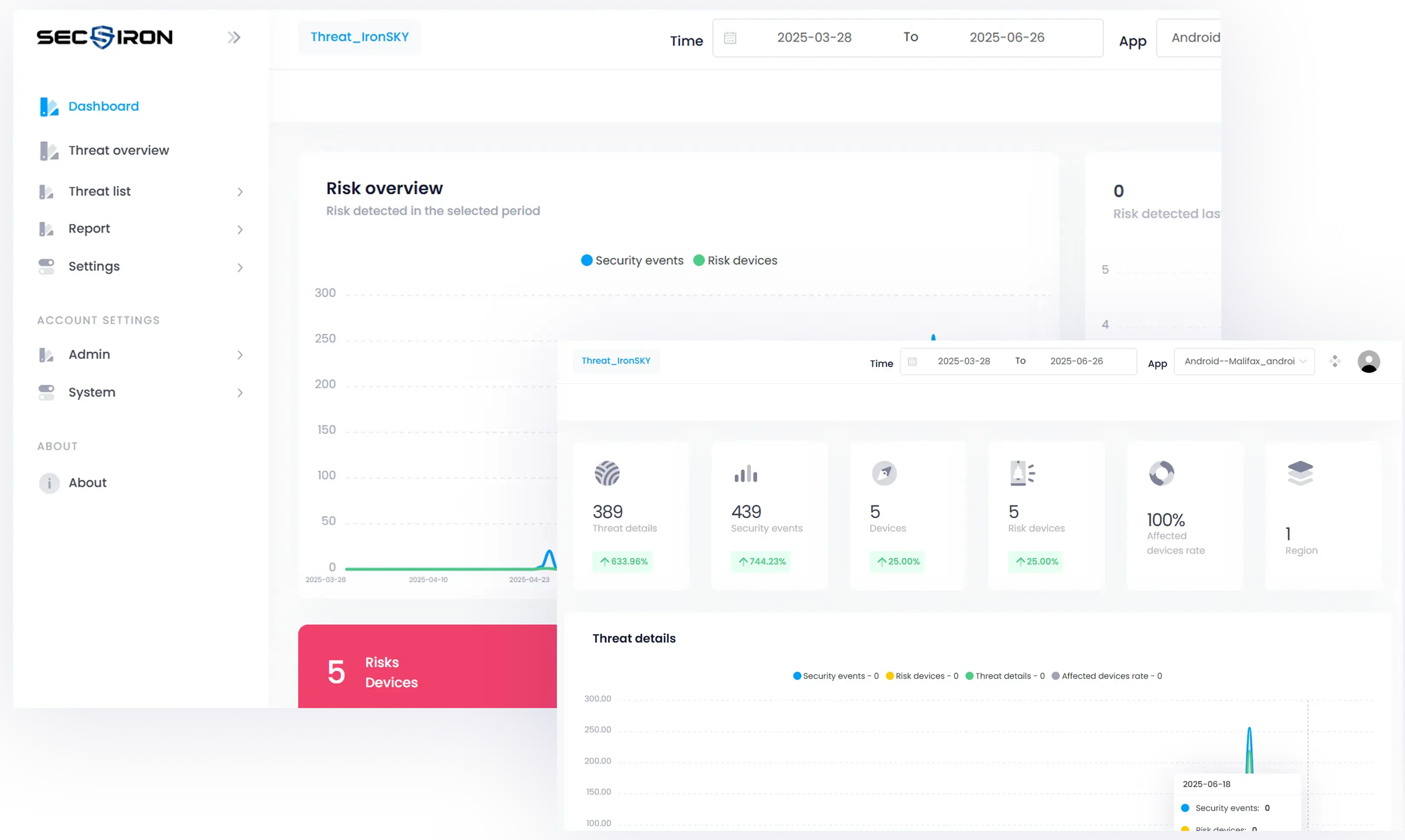
To emphasize the growing need for real-time visibility in mobile app security and position IronSKY as a proactive, intelligent, and always-on solution for monitoring, detecting, and responding to threats before they impact users or operations.
Stay One Step
Ahead Of
Threats
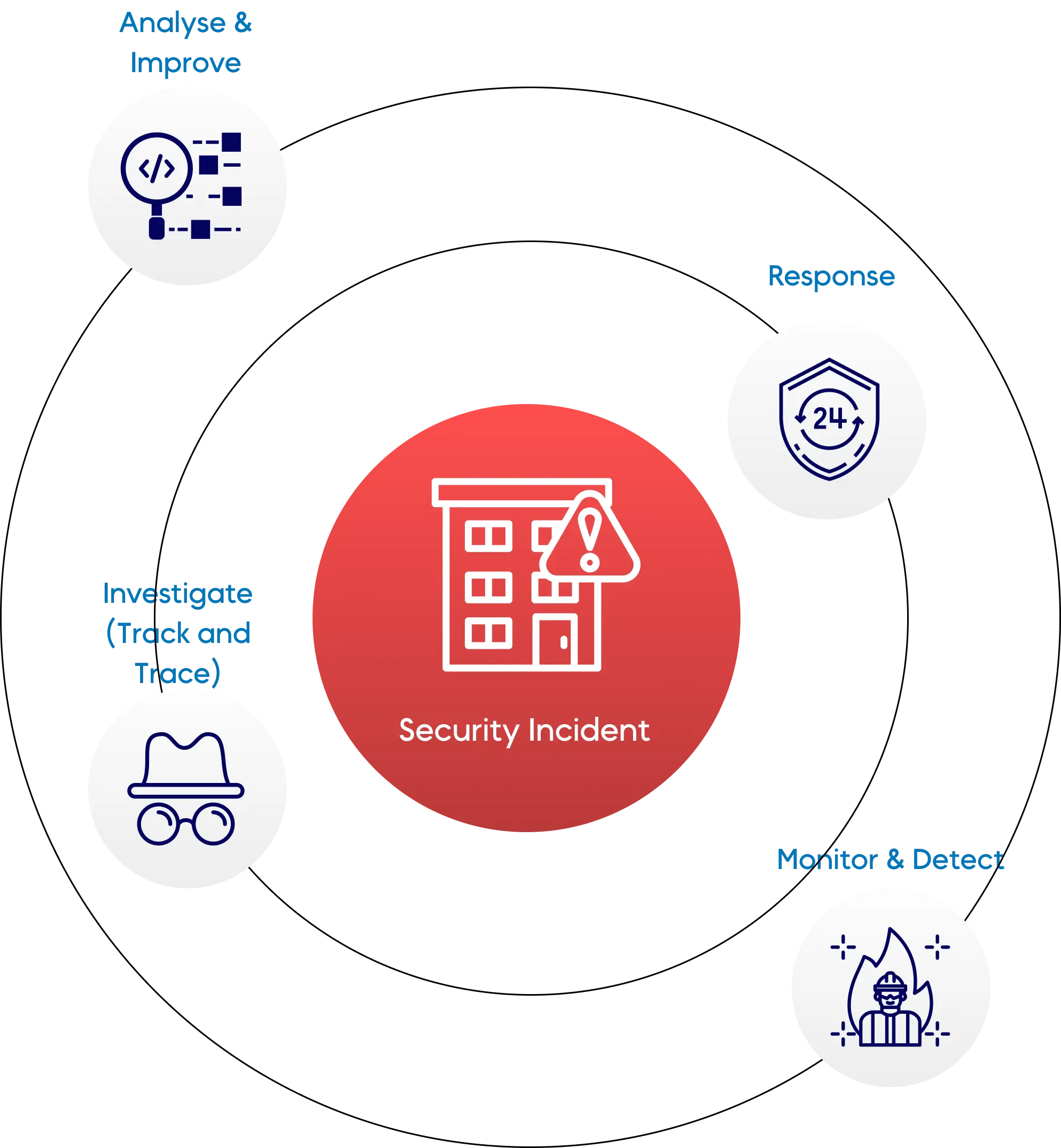
SecIron’s IronSKY is your 24/7 digital watchtower, designed to detect, respond, and learn from mobile security incidents before they escalate.
Detection & Protection Made Smarter
IronSKY is built to spot the things that shouldn't be happening—before they become a problem. From suspicious activity to risky environments, we help you detect and stop threats in real-time.


Threat Detection
Environment Risks
Abnormal Behaviors
Click on any point above to explore more details
Threat Detection
IronSKY catches known and unknown threats before they exploit your app — like:
HTTPS Hijacking
Emulator or fake device use
Code Injection debugging or memory tampering
Time acceleration and proxy spoofing
Even biometric bypass attempts
This means your app stays safe from both common exploits and advanced fraud tactics.
Environment Risks
Not all risk comes from attackers. IronSKY monitors unsafe environments too:
Rooted/jailbroken devices
Risky apps or frameworks
Custom ROMs, VPN tunneling and emulators
Unsafe configurations or hijacked system components
By understanding where and how your app is running, you gain deeper visibility and smarter control.
Abnormal Behaviors
User behavior changes can be red flags. IronSKY flags:
Frequent device or IP changes
Sudden region switches
Account switching patterns
These insights help you detect fraud attempts and account takeovers before they happen.
Benefits That
Go Beyond
Security
SecIron isn’t just about strong security, it’s about making life easier for your developers, your business, and your users.

Supports Android & iOS
You don’t need to change how you work. SecIron fits easily into your app-building process.

3 Layers of Code Protection
Your app’s code stays safe from hackers who try to break in or copy it.

Less Impact to User Performance
Your users won’t notice any slowdowns. The app stays fast while staying protected.

Full Protection, Static & Dynamic
Get strong security at every step — when you build the app and when users are using it.

Flexible Deployment
Use SecIron the way you want — in the cloud, on your own system, or both.
Contact us for
Free Consultation!
Share your challenges, and we'll provide the best solutions for your business, Connecting with us is as simple as clicking a button, and let us come to you.